Lily TechnologiesBitcoin Security Guide
Over the past twelve years, bitcoin has grown from a niche internet currency to one of the largest monetary networks on Earth. The limited supply of bitcoins causes its value to increase as more people decide to preserve their wealth with the digital asset.
But knowing how to secure your bitcoins so that they are not lost or stolen requires expertise in this new area of cryptographic engineering.
This is why we have put together this security guide, so that our customers and customers-to-be understand why we built Lily Wallet and how it protects their coins.
Not your keys, not your bitcoin
Bitcoins are secured by private keys. These keys are random strings of letters and numbers that, through cryptography, allow users to send coins to other people.
This cryptography is the backbone of bitcoin security and possession of private keys is what makes your bitcoin yours and not someone else's.
Therefore it is important that:
- You don't lose your private keys
- Others don't find your private keys
If either of these two things happen, then your digital wealth can be lost forever.
Most bitcoin owners don't actually control their own private keys though. They buy, sell, and hold bitcoin on exchanges like Coinbase or CashApp and hand over control of their private keys to those companies.
For some folks, this is fine. They don't own that much bitcoin or they are using it as a speculative asset to make a quick buck. It would be more work for them to learn how to self-custody their bitcoin than it's worth.
But for those of us who are holding bitcoin for the long-term, relying on a third party custodian to secure our bitcoin becomes more and more risky as bitcoin's value continues to go up.
While self-custody may seem like a big responsibility, it has actually become quite easy for normal people to take full control of their digital wealth in a secure and resilient way thanks to the introduction of hardware wallets and multisig vaults.
The evolution of private keys
Before diving right into it, it's helpful to look at history to see how we got here.
In the early days of bitcoin, users would generate a new private key each time they wanted to receive new coins.
These private keys were either stored on a user's computer where they could potentially be found by malicious software or else they were printed out on a piece of paper and stored in an offline location like a locked file cabinet.

This system forced users to keep track of a lot of data in order to use their bitcoin and it wasn't very secure. In 2012 and 2013, software updates were added to make private key management easier.
The first update, BIP32, introduced what is called hierarchical deterministic wallets. While it sounds intimidating, HD wallets simply allow a user to derive a number of different private keys from one master private key.
The other update, BIP39, standardized a group mnemonic words used to represent the random strings of letters and numbers into a more human readable (and correctable) format. This reduced potential errors when backing up a master private key.
With these two updates implemented, companies like Trezor and Ledger started manufacturing devices called hardware wallets to store users private keys and approve transactions.
This greatly improved bitcoin's user experience and security. Now users can write down one sequence of 24 words to access and recover all of their funds. At the same time, hardware wallets allow users to store their private keys offline and simply plug a device into their computer to approve transactions.
With hardware wallets, private keys now take on a physical form like real keys that people use to lock their cars and houses.

Keys are single points of failure
With the introduction of hardware wallets, not losing your private keys seems pretty trivial to solve. Just don't lose your hardware wallet! Put it in a locked cabinet in your house, engrave your seed phrase into a plate of steel and bury it in the backyard, put your hardware wallet in the safety deposit box at the bank.
While these are all viable solutions, they are still open to failure. What if the house burns down? What if your kids get into the cabinet, steal the device, and lose it? What if the landscapers dig up the steel plate while planting the garden and haul it off to a landfill? What if you lose access to the safety deposit box?
We admit, the odds of some of the situations we listed above are very unlikely. Almost unheard of in fact. But there is a more than 0% chance that they might happen, and if they do, your digital wealth is lost forever.
We could mitigate the risk of losing our private keys by simply making copies of our mnemonic and storing them in different places. If we lose track of our keys in one location, we can go to another spot where we stored them and still maintain control of our money.
While this strategy diminishes the risk of losing our private keys, it increases the likelihood of others finding them. Because of this, simply making multiple copies of your private keys is not a suggested strategy for securing your digital wealth.
The problem we describe above boils down to your private key being a single point of failure. If your private key is lost or stolen then your bitcoins are gone forever.
This is why we tell our customers to:
- Never type your 24 word mnemonic into a computer
- Use a hardware wallet to store your keys offline
But what if we can secure our bitcoin in such a way that removes single points of failure and allows forgiveness in the event that your hardware wallet is lost or stolen?
Over the past few years, the industry has started shifting towards using multisignature vaults to solve this problem.
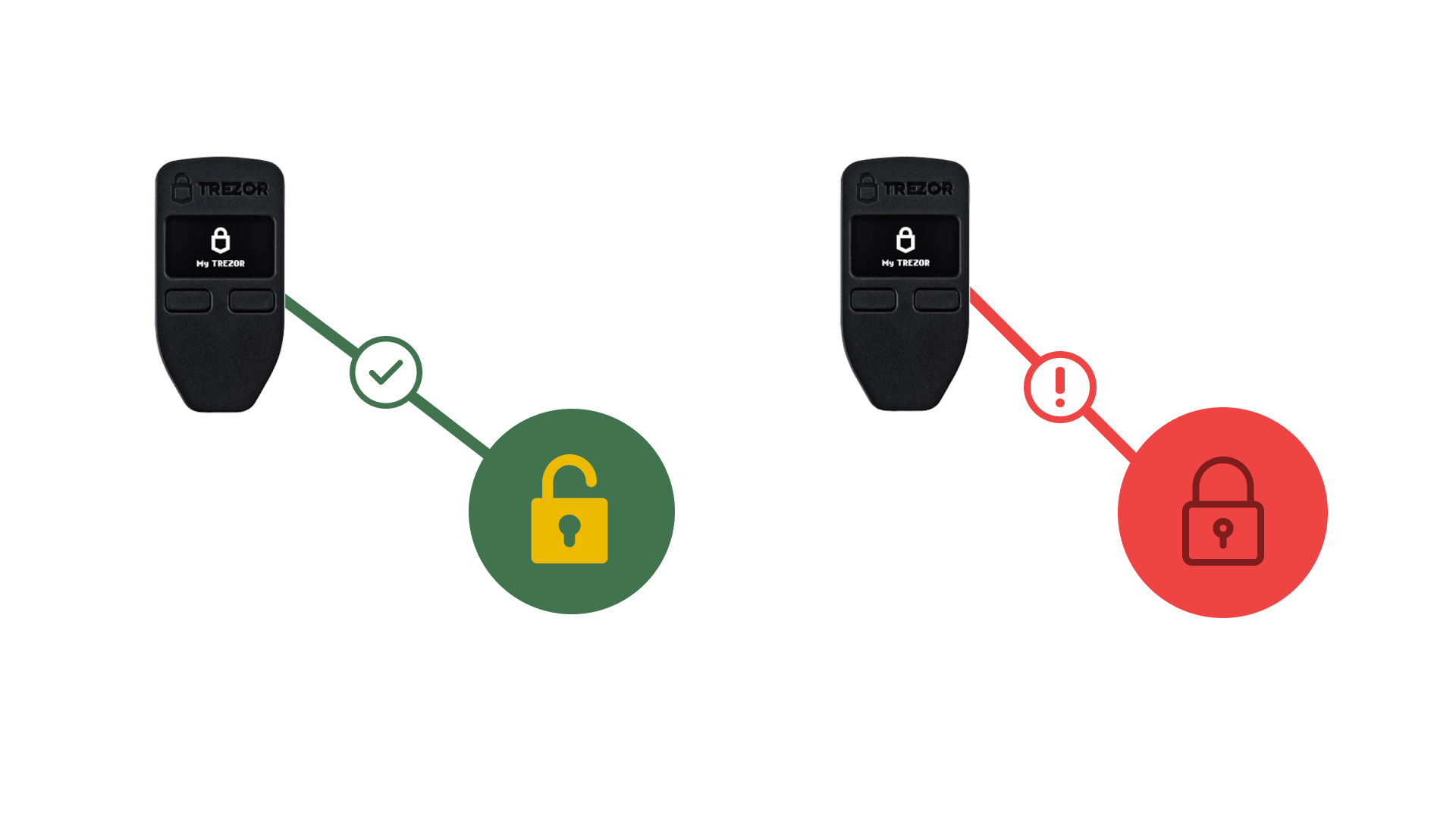
What is multisig?
Multisig combines different private keys together to create addresses that require multiple signatures, or approvals, in order to send coins.
It is a concept that is baked into the bitcoin protocol and exponentially increases the security of your digital wealth.
Most popular multisignature setups are 2-of-3 or 3-of-5. This means that in order to send coins, the transactions must be approved by two of the three or three of the five devices that created the vault.
By having coins controlled by multiple keys in a multisig format, users create redundancy in their security setup and make their digital wealth more resilient than traditional single-key security.
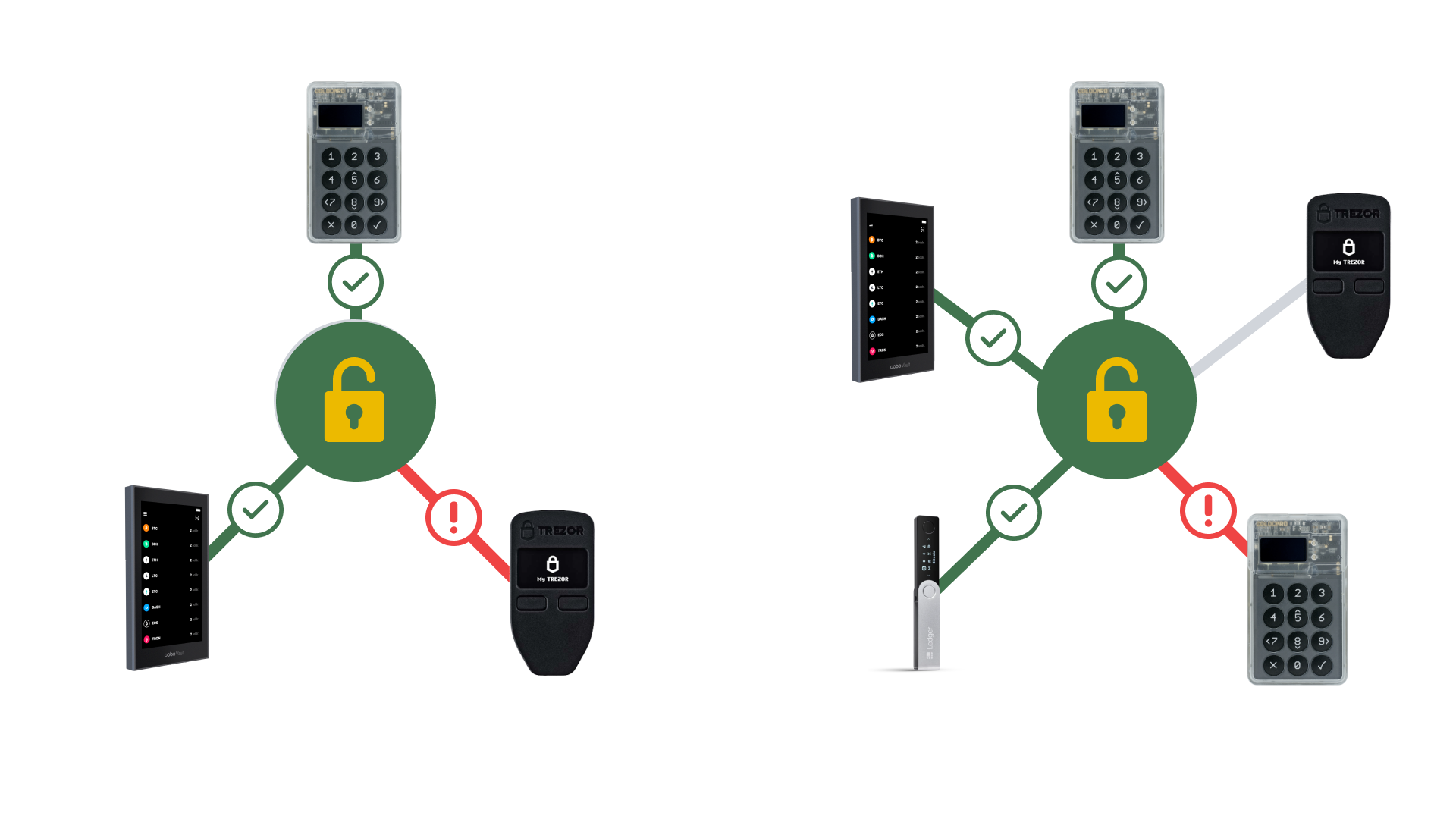
Let's walk through what happens if one of the keys that controls a multisignature vault is lost or stolen:
- After noticing a hardware wallet is missing, purchase a new one from the manufacturer.
- When the new hardware wallet arrives, create a new multisignature vault with the new device and the other devices from the original vault.
- Create a transaction sending coins from the old vault to the new one.
- Approved the transaction with the required number of devices that are still accounted for.
So even though we lost one of our keys, we are still in complete control of our funds and able to move them over to a new vault. This level of resiliency is impossible with a traditional single signature setup.
Other security considerations
While multisig provides resilient security for bitcoin in theory, there are other single points of failure that should be considered when setting up a multisignautre vault.
Use different hardware wallets from different manufacturers
The easiest way to reintroduce single points of failure to your multisig setup is to use the same model hardware wallet from the same hardware wallet manufacturer when creating your multisignature vault.
Hardware wallets from the same manufacturer will likely run the same or similar code to secure your private keys. If there is a critical bug in the code that affects the device's ability to approve a transaction, then users can rely on their other devices to move their funds.
Therefore, Lily Technologies recommends using hardware wallets from different manufacturers when creating your multisignature vault.
Use Coldcard and Cobo Vault in your multisig setup
Both Coldcard and Cobo Vault hardware wallets were built with multisig vaults in mind and provide an extra layer of security from sophisticated attacks involving change addresses.
While these attacks have never been exploited in the wild, we still recommend users incorporate them into their vault setup for peace of mind.
or, verify addresses with other software after setup
If a user decides not to incorporate Coldcard or Cobo Vault into their vault setup, then we recommend verifying addresses and change addresses with other software just in case.
Lily Wallet makes it easy to do this by allowing users to export their vault in formats accepted by other wallet software like Caravan and Bitcoin Core.
Make backups of your software and configuration files
It is important to keep a backup of your wallet configuration in case you lose one of your hardware wallets.
Both Coldcard and Cobo Vault conveniently have MicroSD Card slots for airgapping data between your wallet and the device. We recommend putting a copy of your wallet software and wallet config on a MicroSD Card and leaving it plugged into your hardware wallet.
That way you always have a copy of the software and configuration in case something goes wrong.
Pull blockchain data from your own node
A lot of wallets including Lily Wallet pull blockchain data from a third-party API by default so that users don't have to run their own full node. This is convenient for users who want to use the bitcoin network without running their own infrastructure.
But there is the possibility that those APIs may go offline and prevent you from sending funds.
This is why it is important to have the ability to connect to your own bitcoin node. It provides a guarantee that you will still be able to access your funds even if the wallet you use stops being developed or the data API is offline.
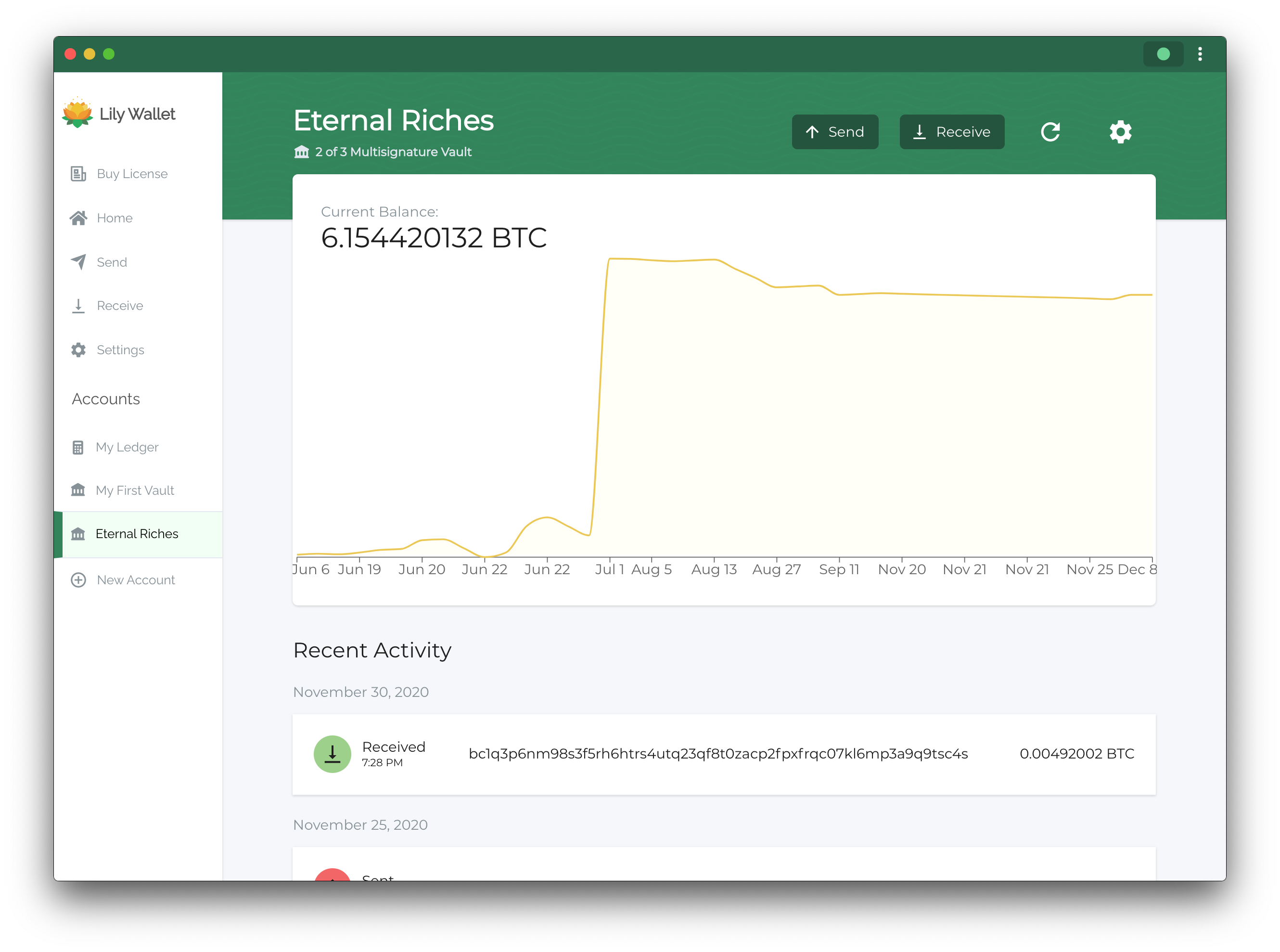
Multisig is easy with Lily Wallet
We built Lily Wallet because we wanted a user friendly way to secure our bitcoin with multisig. We stripped out all of the nitty-gritty details and enforces best practices for our users behind the scenes.
In order to set up a multisig vault using Lily Wallet, simply download the software and go through our vault creation process. It will ask you to plug in or airgap your hardware wallet devices in order to create your vault and can be completed in a few minutes.
After your vault is set up, you can immediately start sending and receiving bitcoin.
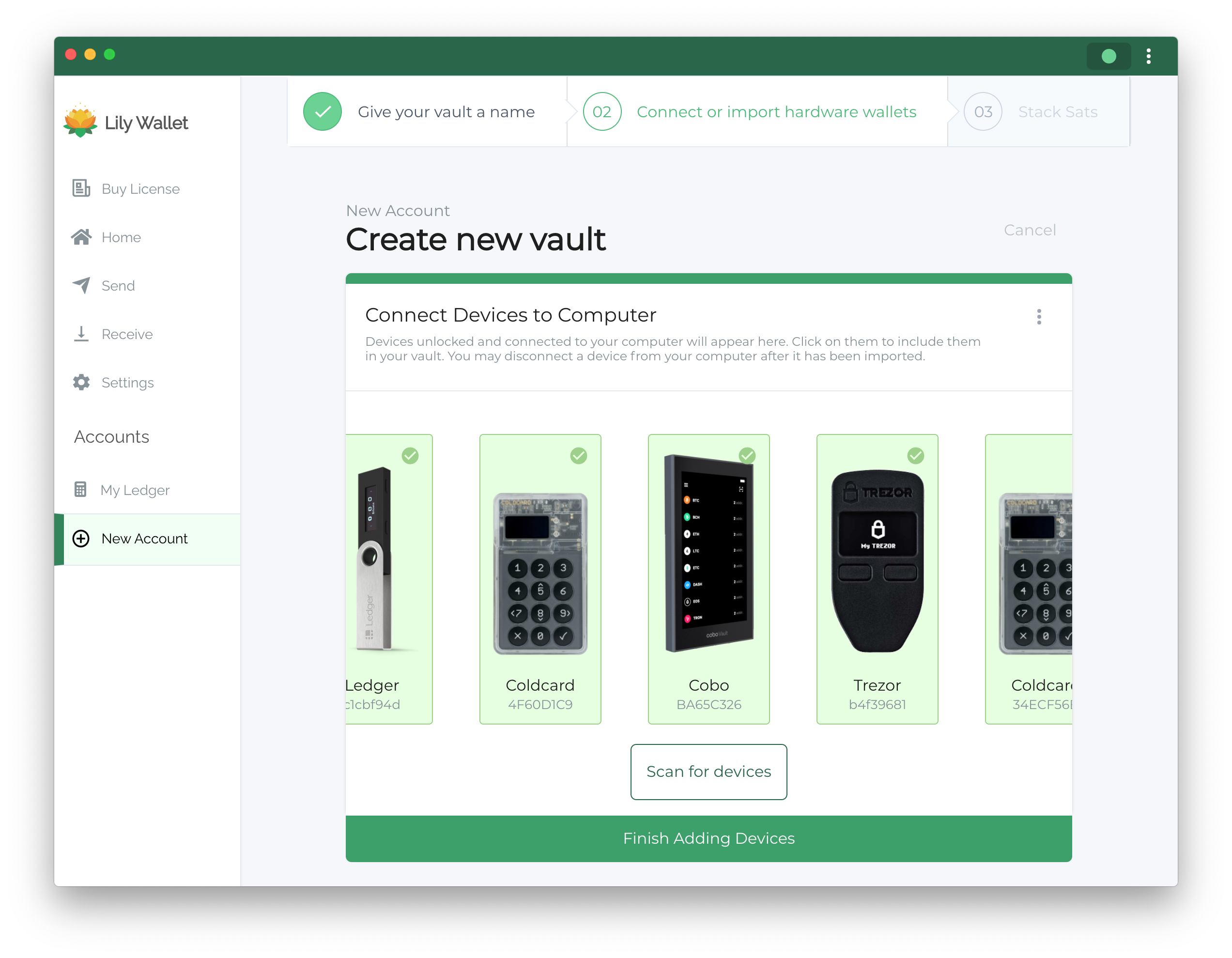
What's more, if you want to upgrade to a first-class bitcoin citizen, you can also connect Lily Wallet to your bitcoin full-node for enhanced privacy and security.
Next steps
We have outlined our thinking about bitcoin security above and have concluded that securing your bitcoin using multisig is the most resilient way to store your digital wealth.
But what are actionable steps users can take today to start securing their wealth?
1) Download Lily Wallet
You can download the latest version of Lily Wallet from our website.
2) Order Coldcard, Cobo Vault, and Trezor hardware wallets
As mentioned above, we recommend using different hardware wallets from different manufacturers.
We personally secure our funds with a multisig vault and store the keys on Coldcard's MK3, Cobo's Cobo Vault, and Trezor's Model One.
3) Setup a multisig vault with Lily Wallet
Once you have received your hardware wallets, set up a multisignature vault with Lily Wallet. We have detailed instructions with images on how to set up Lily Wallet in our get started guide.
If you run into any problems or want an expert to assist you while setting it up, schedule an appointment with a specialist.
4) Store your hardware wallets in different locations
After setting up your vault with Lily, store your hardware wallets in different geographic locations.
We recommend leaving one in a secure location in your house or apartment, another in a safe deposit box at your bank, and another in another location you have access to or with a trusted family member or friend.
Disclaimer: The information in this guide is for educational purposes only and is not financial advice. Please read Lily Technologies terms and conditions.